Online Documentation for SQL Manager for Oracle
SSL
The SSL tab allows you to set up SSL (Secure Sockets Layer) options for your Oracle system in groups: Wallet configuration, Certificate revocation checking, Cipher suite configuration.
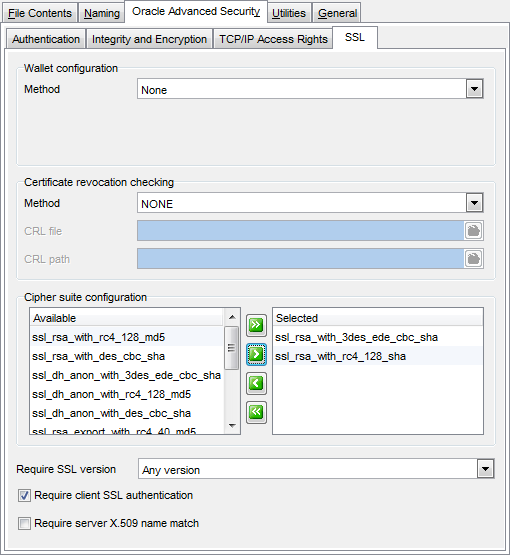
Wallet configuration
Specify the location of wallets - certificates, keys and trustpoints processed by SSL.
Method
Specify the type of storage: none, on the file system, Microsoft certificate store, in Windows registry, entrust wallets.
Directory
Type in or use the ![]() button to specify the location of Oracle wallets (for wallets stored on the file system).
button to specify the location of Oracle wallets (for wallets stored on the file system).
Registry key
Specify the registry key where Oracle wallets are stored (for wallets stored in Windows registry).
Profile / Inifile
Type in or use the ![]() button to specify the path to the wallets profile / inifile (for entrust wallets).
button to specify the path to the wallets profile / inifile (for entrust wallets).
Certificate revocation checking
Method
Use the drop-down list to configure a revocation check for a certificate: select the one of the available methods: NONE, REQUESTED, REQUIRED.
CRL file / CRL path
Type in or use the ![]() button to specify the directory and the name of the file where you can assemble the CRL of Cas for client authentication.
button to specify the directory and the name of the file where you can assemble the CRL of Cas for client authentication.
Cipher suite configuration
Use this group to control what combination of encryption and data integrity is used by the Secure Sockets Layer (SSL).
To select an item, you need to move it from the Available list to the Selected list. Use the ![]()
![]()
![]()
![]() buttons or drag-and-drop operations to move the items from one list to another.
buttons or drag-and-drop operations to move the items from one list to another.
Require SSL version
Use the drop-down list to select the required SSL version: Any version, 2.0, 3.0.
![]() Require client SSL authentication
Require client SSL authentication
Use this option to force the selected version of the SSL connection. Clients and database servers must use a compatible version.
![]() Require server X.509 name match
Require server X.509 name match
Use the option to enforce that the distinguished name (DN) for the database server matches its service name. If you enforce the match verifications, then SSL ensures that the certificate is from the server. If you select to not enforce the match verification, then SSL performs the check but allows the connection, regardless if there is a match. Not enforcing the match allows the server to potentially fake its identify.



































































