Online Documentation for Data Pump for InterBase/Firebird
SSH tunneling options
SSH (Secure Shell Host) protocol is used to heighten computer security when working with Unix systems on the Internet. SSH uses several encryption algorithms of different reliability. The spread of SSH is also related to the fact that a number of *nix operating systems (e.g. FreeBSD) include SSH server in their standard distributions. To learn more about SSH, please visit http://openssh.org.
The SSH tunneling feature of Data Pump is a means of ensuring secure connection to Interbase/Firebird servers when working over insecure connection channels. You can also use SSH tunnel to get access to the remote Interbase/Firebird servers when port 3306 is closed for external connections for some reasons.
The connection via SSH tunnel works in the following way.
First, a connection is established and the process of authentication between SSH client built in Data Pump and remote Interbase/Firebird server is performed. Then all incoming and outgoing information between the application and Interbase/Firebird is transmitted through SSH server with the help of a communication port (regularly port 22), and SSH server transfers this information directly to Interbase/Firebird server.
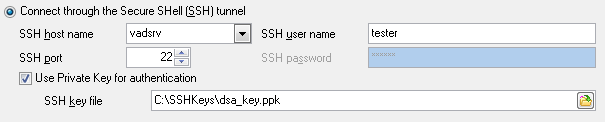
To setup the connection via SSH tunnel, input the following values in the corresponding fields:
- SSH host name is the name of the host where SSH server is running
- SSH port indicates the port where SSH server is activated
- SSH user name stands for the user on the machine where SSH server is running (Note: it is a Linux/Windows user, not a user of Interbase/Firebird server)
- SSH password is the Linux/Windows user password
Please note that Interbase/Firebird host name should be set relatively to the SSH server in this case. For example, if both Interbase/Firebird and SSH servers are located on the same computer, you should specify localhost as host name instead of the server external host name or IP address.
![]() Use Private Key for authentication
Use Private Key for authentication
If the SSH encryption is enabled on the SSH server, a user can generate a pair of cryptographic keys (the Private key and the Public key). The Public key is placed on the SSH server, and the Private key is the part you keep secret inside a secure box that can only be opened with the correct passphrase (or an empty string as the passphrase). When you wish to access the remote system, you open the secure box with your passphrase (if any), and use the private key to authenticate yourself with the Public key on the remote Linux computer.
SSH Key file
Specify the location (the secure box) of the Private key file on your local machine.
Supported Private Key file formats are:
OpenSSH
Putty
SSH.com
Note that you need to trust your local machine not to scrape your passphrase or a copy of your Private key file while it is out of its secure box.