Online Documentation for SQL Manager for PostgreSQL
Changing HBA File
The Host-Based Authentication File tab of the Server Configuration manager allows you to set parameters for Host-Based authentication.
In addition to the postgresql.conf file already mentioned, PostgreSQL uses two other configuration files which control client authentication - pg_hba.conf and pg_ident.conf. Each parameter can be edited and enabled for the database system to take effect. To obtain more information on specific parameters, refer to PostgreSQL documentation.
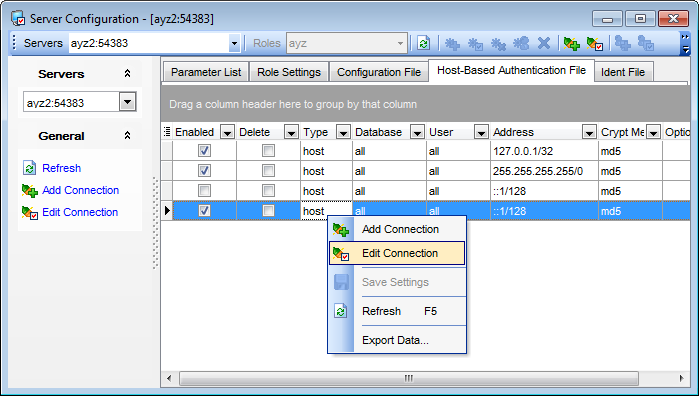
The Host-Based Authentication File list displays the parameters as a grid with the following columns: Enabled, Delete, Type, Database, User, Address, Crypt Method, Option. If more convenient, you can change the order of the columns by dragging their headers horizontally.
Click a column caption to sort items by values of this column in the ascending or the descending mode.
If necessary, you can group the data in grid by any of the columns. This operation is performed by dragging the column header to the gray "Group by" box area at the top. When grouping by a column is applied to the grid, all the rows are displayed as subnodes to the grouping row value. To reverse grouping, just drag the column header back.
Right-click an item within the list to call the context menu allowing you to refresh the list, add/edit a connection, or save current settings.
With the help of General bar you can Add or Edit selected connections; to edit an existing connection simply double-click it.
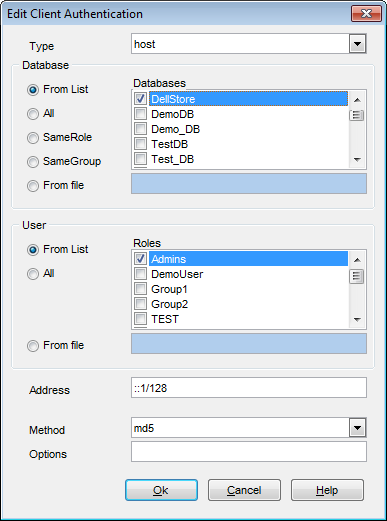
Type
local
This record matches connection attempts using Unix-domain sockets.
host
This record matches connection attempts made using TCP/IP. Host records match either SSL or non-SSL connection attempts.
hostssl
This record matches connection attempts made using TCP/IP, but only when the connection is made with SSL encryption.
hostnossl
This record type has the opposite logic to hostssl: it only matches connection attempts made over TCP/IP that do not use SSL.
Database
Specifies which database names this record matches.
User
Specifies which database role names this record matches.
Address
Specifies the client machine IP address range that this record matches.
Method
Specifies the authentication method to use when connecting via this record.
trust
Allow the connection unconditionally. This method allows anyone that can connect to the PostgreSQL database server to login as any PostgreSQL user they like, without the need for a password.
reject
Reject the connection unconditionally. This is useful for "filtering out" certain hosts from a group.
md5
Require the client to supply an MD5-encrypted password for authentication.
crypt
Require the client to supply a crypt()-encrypted password for authentication.
Note: this option is recommended only for communicating with pre-7.2 clients.
password
Require the client to supply an unencrypted password for authentication.
krb5
Use Kerberos V5 to authenticate the user. This is only available for TCP/IP connections.
ident
Obtain the operating system user name of the client and check if the user is allowed to connect as the requested database user by consulting the map specified after the ident key word.
pam
Authenticate using the Pluggable Authentication Modules (PAM) service provided by the operating system.
To obtain more information on specific parameters, refer to PostgreSQL documentation.
|
See also: |



































































