Online Documentation for SQL Manager for SQL server
Security options
The Security section of the Server Properties dialog allows you to configure the instance of Microsoft® SQL Server by setting options pertaining to server security in groups: Server Authentication, Login auditing, Server Proxy Account, Other security options.
Server Authentication
![]() Windows Authentication mode
Windows Authentication mode
When a user connects through a Microsoft® Windows user account, SQL Server validates the account name and password using information in the Windows operating system. This is the default authentication mode, and is much more secure than the mixed mode. Windows Authentication utilizes Kerberos security protocol, provides password policy enforcement in terms of complexity validation for strong passwords, provides support for account lockout, and supports password expiration.
![]() SQL Server and Windows Authentication mode
SQL Server and Windows Authentication mode
This option enables the mixed mode and allows users to connect using either Windows Authentication or SQL Server Authentication. Users who connect through a Windows user account can make use of trusted connections that are validated by Windows.
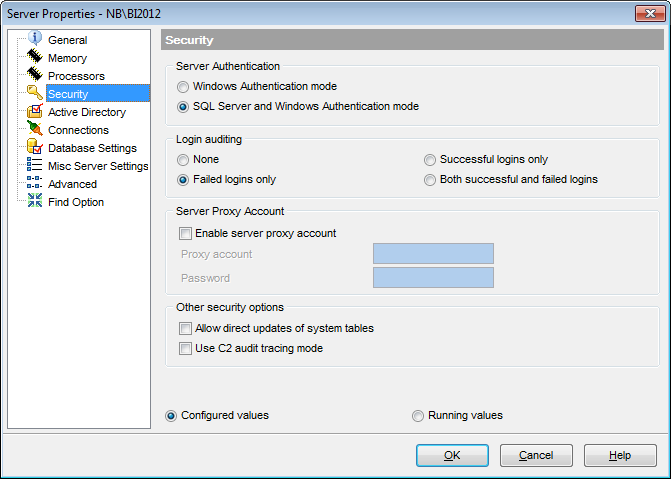
The Login auditing property exposes SQL Server Authentication logging behavior:
![]() None (does not log authentication attempts)
None (does not log authentication attempts)
![]() Successful logins only (logs successful authentication)
Successful logins only (logs successful authentication)
![]() Failed logins only (logs failed authentication)
Failed logins only (logs failed authentication)
![]() Both successful and failed logins (logs all authentication attempts regardless of success or failure)
Both successful and failed logins (logs all authentication attempts regardless of success or failure)
Server Proxy account
This option allows SQL Server users that do not belong to the sysadmin fixed server role to execute xp_cmdshell commands and to own SQL Server jobs. To get access to this feature, you must enter Proxy account name and Password.
Note that this option is only available when you use SQL Server 2005 (and higher). The login used by the server proxy account should have the least privileges required to perform the intended work. Excessive privileges for the proxy account could be used by a malicious user to compromise your system security.
Other security options
![]() Allow direct updates system tables
Allow direct updates system tables
Turn this option on to modify system tables directly.
Note: System tables should not be changed directly by any user. It is not recommended to modify system tables with DELETE, UPDATE, INSERT statements or user-defined triggers.
![]() Use C2 audit tracing mode
Use C2 audit tracing mode
Selecting this option will configure the server to record both failed and successful attempts to access statements and objects. This information can help you profile system activity and track possible security policy violations.



































































